End of the college entrance examination, anxious parents may receive from the "Ministry of education" a text message telling you can score App query, along with the download link.
618 shopping season approaching, chop hand party may receive 200 Yuan "red envelopes", and prompts you for a long time cell phone red can be used to offset the purchase price.
In the descent of the Sun, ginger evening smoke, Liu Shizhen CP how would what gesture of cruelty to dogs, kinky fans may search a link to Web site, want to download all prerelease episodes.
When you have the eagerness was opening the doors of the online world, is likely to be a Trojan horse disguise.
Trojans are one of the variations in the world's fastest-growing species, black or gray industrial chain-led economy these "poisonous insects" sleepless night stormed to evolve.
What exactly are these Trojans pose lurking in the corner of our life, is what posture suddenly from the thighs to bite off a piece of meat? In this connection, Tencent computer security expert Liu Guize Butler has a say. Because he was at the helm of "Hubble platform" specifically for the computer Manager provides anti-virus engine, hand edged Trojan is right up their alley.

"Tencent computer head Liu Guize Butler Hubble platform"
Biography of the series and the descent of the Sun can spread Trojan
Liu Guize told Lei Feng network, clings to hot events is not a new phenomenon. On find a Trojan authors will do everything it can to grab interest, capture the current hot spots is their "basic skills". As long as you desire or fear, let you successfully downloaded the Trojan, the first step is done.
Whether it is double 11, 12, or 618, shopping Carnival activities of national interest, almost all the monsters to come to "Gold Digger." This activity not only in the large crowd of, and in such cases the user is easy to let down their guard.
In addition, the examination or year fixed social events for example, for a particular user, it is the annual "catastrophe." Of course, the current hit series--such as the year of the series, and today the descendants of the Sun--will also become a trap. Eager to know the story of the development of fans tend to lose my eyes, download a bunch of malicious software still won't regret.
"After the download of the descendants of the Sun, strange appeared on the desktop shortcut/image from the Hubble platform provides a Web page"
In short, as long as the large number of people involved in something, without all kinds of Trojans and their flaming trap.
The beginning of the story are similar to those of innocent children's shoes due to various reasons to download Trojan. Next, they will see a variety of "vicious" things happen on themselves.
Lock extortion
If you lock in blackmail Trojans, then congratulations, you almost touch the "Crown of the Trojans". In the case you don't know, all the documents and photos on your computer are encrypted. And when you realize that when this happens, and suddenly pops up an alert box will see: your file has been locked, to transfer to my account 1 bitcoin can unlock the document. (1 coins roughly 3000 RMB, of course, different races and schools of Trojans demanding the ransom may be different. )
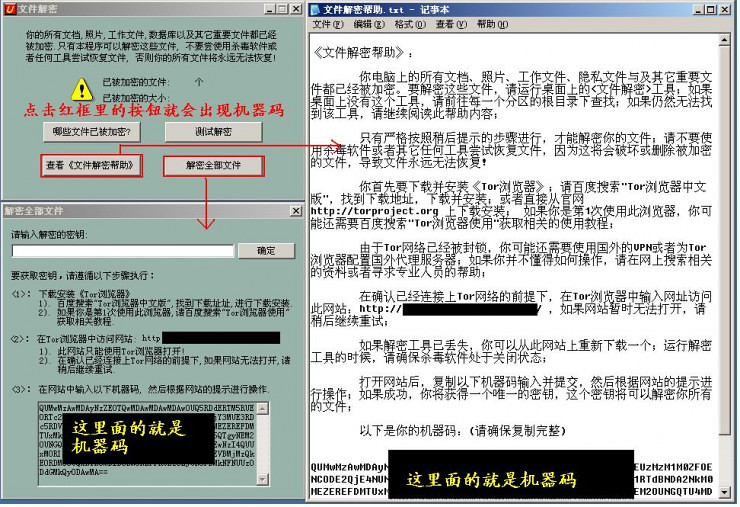
"A Chinese-language key lock Trojans interface of blackmail and extortion"
This key locks the Trojans starting from the second half of 2015 "fire", at the beginning we detected some Trojan German, English version soon appeared, came to the Spring Festival the traditional Chinese version, appeared again in the first half of this year Chinese Simplified lock blackmail Trojans. You can clearly feel the rhythm of this type of horse evolution.
Liu Guize said.
According to statistics of Hubble, a blackmail Trojan outbreak at its peak when the computer can infect nearly 10,000 times a day. Lei feng's network had a lock on going on around us blackmail Trojan outbreak made a detailed report, interested in children's shoes can be of the of the of the stamp here.
Fraud Trojan
Because users are often deceived State download such Trojans, so for the sensible lurking on your cell phone or computer, they often offer some users are looking for "normal function"-for example, enjoy the little things.
However, this type of Trojan's main function is to collect your personal information as detailed as possible.
Mentioned before "college entrance examination results queries App" for example, the user can never be successfully installed this App, and prompts the user to "install failed" is part of a conspiracy. User installation fails, relaxed their vigilance. In fact, the Trojans have been entrenched in the background, silently takes your contacts and messages, and then find the "father, mother, elder sister," and other important contact information with your bank card number, home, lifestyle information such as text messaging, returned in conjunction with cheat master server.
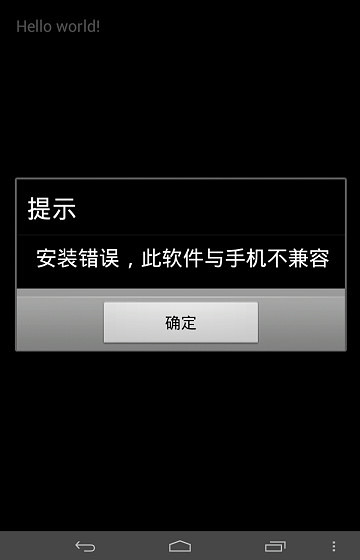
"College entrance examination results queries App" failed install "screen/image from the Hubble platform"
Based on these extremely sensitive information, cheats can mount a fraud targeted to one person. One can say that your home address and your life and hobbies, and who know your loved one, you can easily get your trust, then cheats will pull out all the tricks are familiar Telecom fraud.
Ad Trojan
Liu Guize told Lei Feng network, this Trojan is the most rampant recent category, 30% to 40% of the total accounted for Trojans, but also in a situation of increasing month by month.
These Trojans don't make money from the infected, but earned promotion from the advertisers.
This type of wool in the pig business thinking is the essence of the Internet is well know by black industry. This type of Trojan is also raging in two major PC and mobile platforms, on the phone, they generally disguised as users need software, but used in the process, they secretly accepting remote control, to silently install a bunch of other App users.
This App is probably not malicious, but merely promote the App needs. They hope that through various channels to promote their own, eventually, such a task is part of the Trojans who falls in the gray industrial. The Trojans to promote and push in the word is the same.
Liu Guize told Lei feng's network (search for "Lei feng's network", public interest), Hubble platform recently warning killing an advertising Trojan that erupted, his junior partner to the Trojan named "shadow."
"I think this name is very vivid. Shadow represents uncertainty, the mouse is shady. The Trojans do something very simple, is your computer all advertising channels into his browser navigation page. Users have no sense of any change to the navigation interface, accessed through the navigation of the Web site and there is no change. But changes have taken place behind the access channels, so that the website promotion costs will flow into the hands of Trojans users.
This Trojan May 23, was captured by the system, we'll study and issued a killing rules, sample size, only 100,000 of the whole network at the moment. Due to rules issued to the force needs a certain amount of time, until the next morning when the whole network of eruption rate soared to over 400,000, until Butler began scanning the computer, the "epidemic" under control. Kenzo iPad Mini
Above the three most rampant kinds of Trojans scene this month of the Top3. Liu Guize said, the past year can clearly see a black "closer." Previous theft, Trojans, after stealing QQ number and password, such as QQ not carrying coin Q virtual property, then we have "hit" means such as, for example, try to use the same account number, password email, Taobao, East can finally "get" it.
It now appears that Trojans "boss"-the black hat hackers still find traditional approaches accuracy is not high, and a waste of time and explores the "distinctive new development paths".
Trojan war
Avira Virus, Trojan horse, is actually behind them and black people. It is an endless "confrontation". They are constantly changing, "technical", we also continue to unravel their "modus operandi".
Liu Guize and team found that recent races of different genres of Trojans, "uniting" two very special "moves".
Stealth Kenzo mini case
Keep yourself alive longer, is the pursuit of the Trojan. Even if able to spend half a day on computers, cell phones, and even stay for half an hour, you can steal user information, promoting his "friends". Can game longer and antivirus software, no immediate effort to study new varieties against encirclement and own anti-virus software.
Due to Hubble's main method of machine rule is used to detect virus Trojan, so there are a large number of files daily samples will undergo screening of Hubble. However, the Hubble team found an interesting phenomenon. That is, there are some programs, run in the virtual environment without any function, nor do any action.
Come on you is a software, you don't do anything after it has been installed exactly why? You visit a Web page ...
Researcher crashes on the inside, does anyone really boring to write a program that doesn't do anything for you? Acute sense of smell tells them, that there must be "trick".
Sure enough, after careful investigation they found that this type of Trojan is run, the first thing to do is "silent".

"Silent periods ranging from a few minutes to tens of minutes, the longest a Trojan was silent for an hour. "Liu Guize said," in order to improve the efficiency of detection platforms not detected in 60 minutes on the same file, the default setting is usually second-level. If traditional manual auditing code, and it may take more than 10 minutes to tens of minutes. And now the Trojans after severe confusion encrypted code, even can do perform and decryption, so manual audit of efficiency is very low. "
However, to deal with the tough Trojan, researchers came up with a simple set of rules. That's when Hubble's systems in the detection, in the event of the "silence procedure", and came to skip silent snippet, direct implementation of the truly command operations.
Of course, stealth moves not only "silence". There is also a traditional way of stealth: to hide like a parasite to the document, recently began "hired". A macro is a virus.
Security process is like this, "dark alley" came up with a way, security vendors will continue blocking; and so on, "dark alley" may suddenly find that the first method is useful. Certainly not simply repeat this method, but superimposed the techniques of "upgrades"
Because Office documents sometimes need to display animations or dynamic data and statistics, so in fact the Word or PPT documents actually allow executable code in it. However, due to suffering from macro viruses in the past, in the new version of Microsoft Office will prevent macros from running by default. However, no bottom line and no integrity of the black hat hackers phishing privacy and theft are stacking up. Their practices are:
Figure out your professional and personal information. Then send you a letter to deceptive messages-such as reimbursement of invoice information, industry associations notified, customer order – you have no reason not to open attachments. In the message, a "customer" or "tips" you, I annex inside a quotation, it needs to open a macro when Excel prompts you when a point agree with Oh ~ ~
Lei feng's network said the most valuable trust seems torn ...
Cloud control
Like cruise, stop stalling, reversing radar became the car's standard, "control" has also started to become a standard of the Trojan. As a Trojan horse, if not the cloud control, too shy to go out and greet people.

Liu Guize said, "flexible fast" is cloud control of maximum advantages, it can let Trojans and hacker of server keep real-time of contact, according to specific situation made most precise of reaction: if found you of machine installation of is Windows XP, will immediately issued a for XP of "combat strategy"; If is Windows 7, so on will issued a "Win7 combat plans"; If is phone, also can get.
Moreover, controlled through the cloud, the hacker can even control the life cycle of the Trojan. The victim's computer, for example a day later, the Trojans will be forced to upgrade to the latest version 2.0.
Trojan family updates faster than most people imagine, the fastest 10 minutes updated edition. Call Update, code structure, encrypted format, against the action sequences are subject to adjustment. To effectuate such updates, hacker has the potential to do a lot of Trojans and released according to the rhythm, and Trojans may study a set of automated tools to code transformations.
Gods and demons struggle between
For this kind of thinking indefinite form of Trojan, security experts can only seize the Trojans--the most fundamental features of "acts" are looking for. For the first time to detect the latest Trojans, day and night detection system had to stay awake, 7*24 hours running.
Liu Guize and Hubble team, their task was not to judge a program manually are not Trojans, but use their own experience and understanding to create a section of the recognition rules of the Trojan, and then let the Hubble system to learn the rules. Ever-accumulating rule lets the system for getting close in accuracy of judging the security experts of the Trojan.
Liu Guize judgement of a few simple rules:
1, if a software will give the computer a full scan, but for such a large number of files read-only, still writing, it is quite obvious that lock extortion of behavior. Because the normal overall scan software is not necessary.
2, a piece of software running on the network, this action is justified, but if each network request is some control information, and control information and the software itself, so this is a generalization of suspicious Trojans. Networking such as QQ in the background, must be downloaded and their relevant information, such as the update package. But promoting Trojans and request the General list is a list of software with download, this feature is quite obvious.
3, moving from the supplier, after the normal App to run, once the user click on the Home button, it should go into the silence, just networking reported secretly user data for statistical purposes. If an App has a number of frequent operations in the background, for example, read the privacy information and contacts, even applying to the system message permission to listen (which is generally used in "registration code automatically" on the function of enhancing the user experience). Then the App whereabouts is suspicious.
4, the previously mentioned "the shadow rat" Trojans, which are installed immediately after Setup scans the user's browser, while scanning the user which antivirus software are installed. This behavior is also very suspicious.
Sounds that rule entirely different, judged in black and white. But the biggest difficulty is that Liu Guize said training machine "sure".
Characteristics of the machine is "one is one, and two" best characterized by the people "is not a, and b not two". For example, something, Tom came to me for help, I did, Dick came to me for help, I'll quit. For example, a user is well received by users of the program, it will modify the user registry, that we can't release; and some minor software changes the user's registration form, we may decide it is a Trojan horse program.
The difficulties faced by Liu Guize, and between machines and humans the ability to divide. However, after huge amounts of samples for a large number of trained Hubble's systems are working towards smarter and more "like a man" the direction of evolution. This made Liu Guize is comforting.
Hubble's systems every day to test samples of tens of millions of files, but in the end I still have less than 1000 highly ambiguous file for our researchers. Of course our aim was not to 1000 documents are classified. But by studying the characteristics of these files, work out new rules for the updated system can determine these files. Qianbabaige fuzzy files are generated every day now, maybe by next year at this time, only eight out of ten fuzzy files every day.
In fact, Hubble, researcher for improvement of the rules is still quite effective. Past teams have five rules for development experts, ten samples analysis expert analysts and now there are only two samples, the rest into all the experts rules out.
As long as there is room for profit and people of good will and malicious Trojans will never seem to disappear. In the eyes of Liu Guize, often they are just figuring out a Trojan family, the Trojans broke out. Security experts and Trojan authors have become this endless war the two permanent force.
Since it is impossible to eradicate the evil of humanity, then we might as well look at the gods afraid, more exciting battles.

Read on:
The ransom to the kidnappers on the Internet is a kind of experience? 》
Before the blackmail, hackers how to extort encryption software? 》
The hackers blackmail! One can say your name, telephone number and position of "acquaintance", you may lock your computer
More technical content to refer to the Hubble Tencent anti-virus laboratory analysis system April threat intelligence trend report




